Share this article on:
A hacker has put a database of phone numbers and email addresses belonging to 5.4 million Twitter accounts for sale on the dark web for $30,000.
Twitter is currently investigating the breach according to reports by CyberWire. The hack is linked with a cyber breach that occurred in January this year according to Restore Privacy, after tracking down HackerOne reports that observed the January incident "had potential of exposing user information even when hidden behind privacy settings".
Restore Privacy has also found that Twitter paid a bug bounty to the researcher who had reported the breach, then enabled the short-form social media platform to close it, but that earlier vulnerability appears to have been "exploited to collect a very large tranche of user data".
In an interview with BleepingComputer, the cyber threat actor known as "devil" revealed that "they used a vulnerability to collect the data in December 2021", noting that interested buyers have already expressed interest after advertising that bidding starts at $30,000 for the data.
According to devil, the database "contains info about various accounts, including celebrities, companies, and random users", in an announcement to the stolen data market.
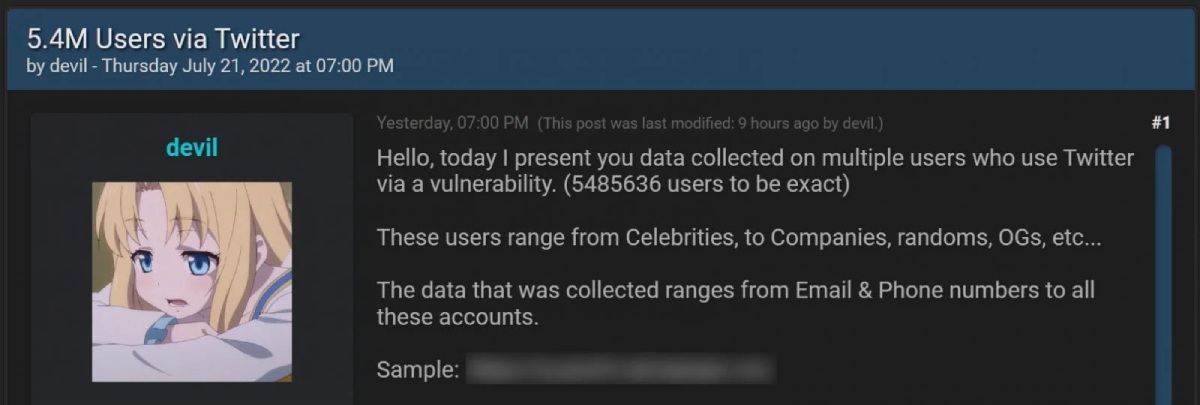
"Hello, today I present you data collected on multiple users who use Twitter via a vulnerability. (5485636 users to be exact)," reads the forums post selling the Twitter data.
"These users range from Celebrities, to Companies, randoms, OGs, etc."
In conversation with BleepingComputer, devil revealed, "you could feed email addresses and phone numbers to the vulnerability to determine if it is associated with a Twitter account and retrieve that account's ID", and staunchly declined association with zhirinovskiy and denied using HackerOne.
"I don't want to white hat in trouble who reported it on H1," devil continued.
"I guess a lot of people are trying to connect him to me, I would be pissed if I was him.
"So I can't stress this enough I have nothing to do w him nor H1," the threat actor told BleepingComputer.
This vulnerability is similar to how threat actors scraped the Facebook account data of 533 million users in 2021.
We are reviewing the latest data to verify the authenticity of the claims and ensure the security of the accounts in question.”
A Twitter spokesperson told The Record that the company is investigating the incident.
"We received a report of this incident several months ago through our bug bounty program, immediately investigated thoroughly and fixed the vulnerability.
"As always, we’re committed to protecting the privacy and security of the people who use Twitter.
"We’re grateful to the security community who engages in our bug bounty program to help us identify potential vulnerabilities such as this," the Twitter spokesperson told The Record.
The short-form social media platform is looking into these recent claims, according to the Twitter spokesperson, who confirmed during the interview with The Record that the company is verifying the authenticity of the claims to ensure the security of the accounts in question.
According to BleepingComputer, "it is impossible to say if all 5.4 million accounts being sold are valid" after conducting a verification exercise, looking into a number of Twitter users listed in a small sample of data shared by the hacker. BleepingComputer reported a "small number of users were verified from the scraped data", which means the "email addresses and phone numbers may not be accurate".
BleepingComputer added that threat actors can use the "email addresses and phone numbers in targeted phishing attacks, even though most of the data being sold is publicly available", warning that all Twitter users should be vigilant.
[Related: Cyber actors continue campaign against supply chain and third-party suppliers]