Share this article on:
Ransomware attacks continued to be a significant threat to industrial organisations and infrastructure in the first quarter of 2023, underscoring ransomware groups’ continued growth in sophistication and opportunism.
As such, it’s crucial industrial organisations remain vigilant and adopt robust cyber security measures to protect their operations and infrastructure. Twenty of the 61 ransomware groups that we track caused significant damage to industrial organisations through the use of continually evolving tactics.
In this first quarter, we observed two new and significant trends. First, the use of zero-day vulnerabilities. Second, the exploitation of recently discovered vulnerabilities. For example, in February, the Clop ransomware group claimed use of the GoAnywhere zero-day vulnerability (CVE-2023-0669) to impact 130 organisations. Dragos is aware of 14 industrial organisations that this group impacted, although it is unclear if the group used the GoAnywhere vulnerability. Other ransomware groups, such as Cuba and Play, used a zero-day exploit dubbed OWASSRF to target CVE-2022-41080 and compromise unpatched Microsoft Exchange servers.
Dragos detected 214 ransomware incidents, a 13 per cent increase on the previous quarter. The impact of ransomware attacks on industrial organisations is more difficult to counter and disruptive than in previous quarters. For example, the Copper Mountain Mining Corporation (CMMC) was impacted by AlphaV ransomware, prompting the isolation of the ICS/OT network and a switch to manual operations. Meanwhile, the Dole food company had to temporarily shut down production plants in North America due to the impact of a ransomware attack on their IT system.
The motives behind ransomware attacks can vary widely and are often difficult to confirm with certainty. However, multiple factors can significantly drive ransomware activity, including financial gain, geopolitical tensions, and economic conditions.
To combat the ransomware threat, governments are increasing efforts and regulations. One example in the US was the establishment of the Ransomware Vulnerability Warning Pilot (RVWP) by the Cybersecurity and Infrastructure Security Agency (CISA), which is a requirement of the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA). As part of the RVWP, CISA leverages existing authorities and technology to proactively identify information systems with security vulnerabilities commonly associated with ransomware attacks.
Dragos analyses ransomware variants impacting industrial organisations worldwide and tracks ransomware information via public reports and information uploaded to or appearing on dark web resources. By their very nature, these sources report victims that allegedly pay or otherwise “cooperate” with the criminals. However, there is no 1:1 correlation between total attacks and those that elicit victim cooperation.
Our breakdown of ransomware activities for this quarter follows.
Ransomware by region
Globally, 44 per cent of the 214 ransomware attacks impacted industrial organisations and infrastructure in North America, for a total of 95 incidents. Within North America, the US sustained over 41 per cent of all ransomware attacks. Europe came in second with 28 per cent of the global total and 59 incidents, followed by Asia with 15 per cent or 33 incidents. South America had 5 per cent (10 incidents), the Middle East 4 per cent (eight incidents), Africa 3 per cent (six incidents), and Australia just 1 per cent (three incidents).
Ransomware by sector and subsector
Sixty-seven per cent of ransomware attacks impacted the manufacturing sector (143 incidents), the same as the previous quarter. Food and beverage was next with 13 per cent of attacks (28 incidents), roughly double the incidents in the previous quarter. The energy sector was targeted with 7 per cent of the attacks (15 incidents), and the pharmaceuticals sector had 5 per cent (10 incidents). Oil and gas showed 3 per cent (seven incidents, up from four last quarter), and the transportation sector around 3 per cent (six incidents). Mining and water sectors were impacted, with 1 per cent of total attacks.
The industrial ransomware incidents that we tracked impacted 36 unique manufacturing subsectors. At the top of the list was building materials manufacturing with 14 per cent (20 attacks), followed by the automotive manufacturing sector with 10 per cent or 14 attacks. The remaining manufacturing subsectors that were impacted are illustrated in Figure 1 below.
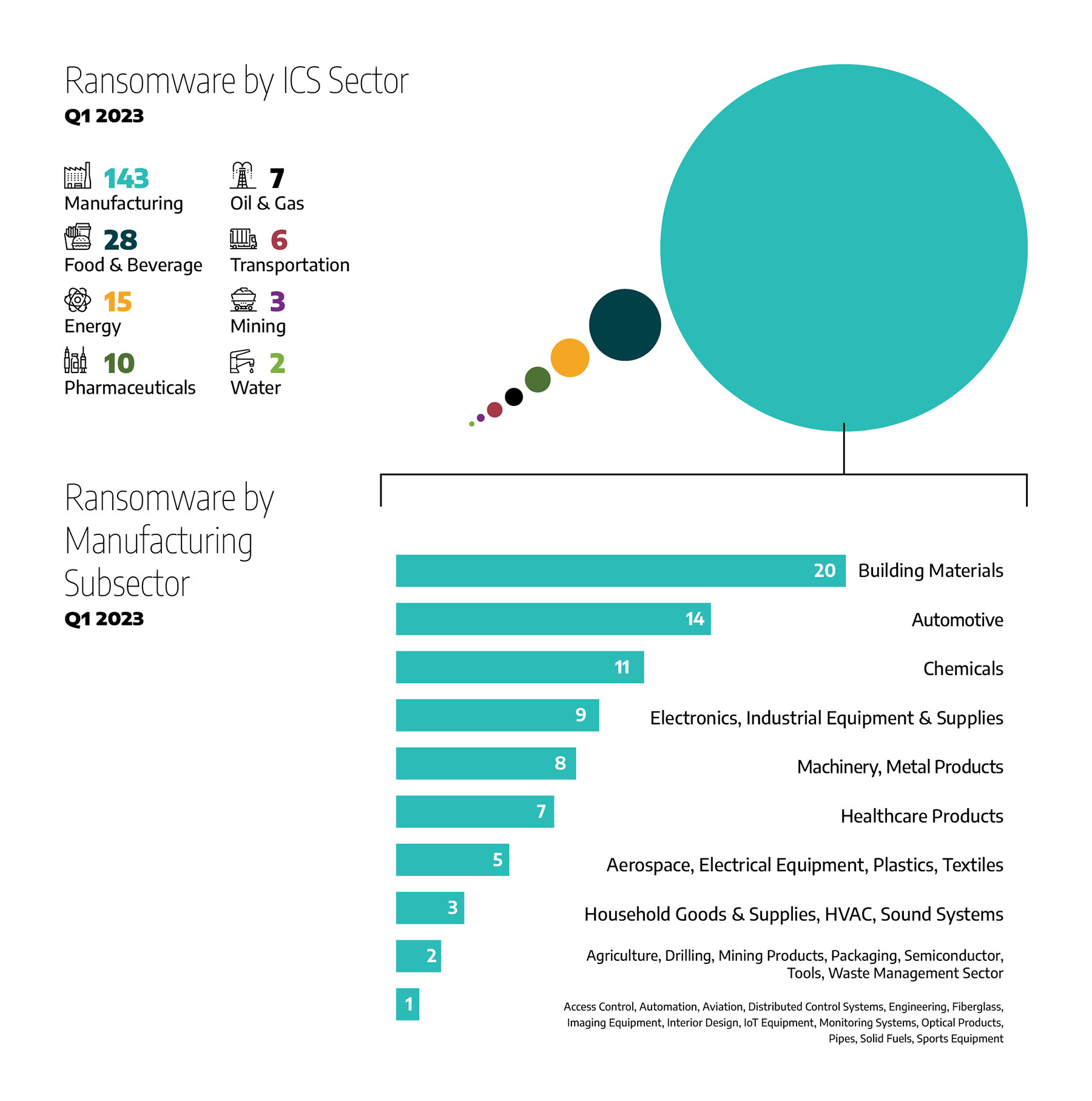
Figure 1: Ransomware incidents by sector
Dragos tracked the activity of 20 ransomware groups, compared to 24 in the previous quarter. Analysis of ransomware data shows Lockbit 3.0 was responsible for 36 per cent of the total ransomware attacks, accounting for 77 incidents, nearly double the incidents in the last quarter; AlphaV was responsible for 13 per cent of attacks; Royal came in next with 12 per cent; Black Basta and Clop next with 7 per cent each, and Play with 5 per cent. The remaining attackers are shown in Figure 2 below.
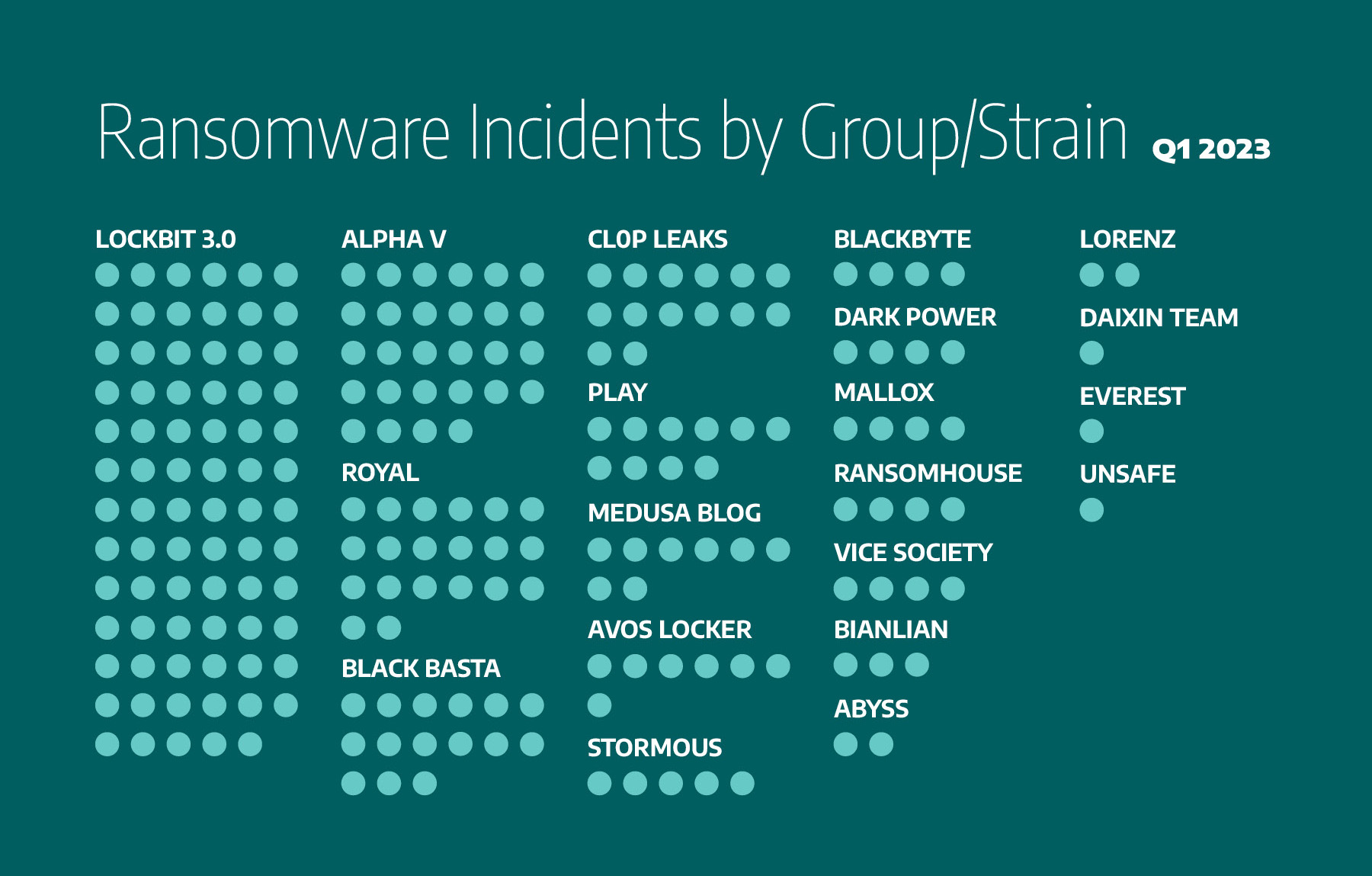
Figure 2: Ransomware incidents by ransomware group
Ransomware victimology trends
Dragos continued to observe trends in the victimology of ransomware groups. This does not, however, determine the permanent focus of these groups, as victimology can change over time. Dragos observed three more ransomware groups impacting industrial sectors and regions in this last quarter than in Q4 2022. Based on our analysis of the Q1 2023 time frame, we observed some of the most active ransomware groups impacting the following industries and geographies:
There were also groups we observed in Q4 2022 but not in Q1 2023, and vice-versa. We also observed the following ransomware groups for the first time this year: Medusa Blog, Dark Power, and Unsafe. It is unclear if these new groups are entirely new or reformed from other groups.
We assess with high confidence that ransomware will continue to disrupt industrial operations, whether through the integration of operational technology (OT) kill processes into ransomware strains, flattened networks allowing ransomware to spread into OT environments, or precautionary shutdowns of production by operators to prevent ransomware from spreading to industrial control systems. Due to the changes in ransomware groups, we assess with moderate confidence that new ransomware groups will continue to appear as either new or reformed ones in the next quarter.
Further, as ransomware groups’ revenues continue to decrease due to victims’ refusal to pay ransoms and government efforts to prohibit this, we assess with moderate confidence that ransomware groups will increase their efforts to cause damage to industrial organisations to fulfil their financial objectives.
Abdulrahman H Alamri is Senior Adversary Hunter at Dragos.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.