Share this article on:
Check Point Software analysts have seen an increase of threat groups leveraging war-themed documents on the Russia-Ukraine conflict to spread malware and lure victims into cyber espionage.
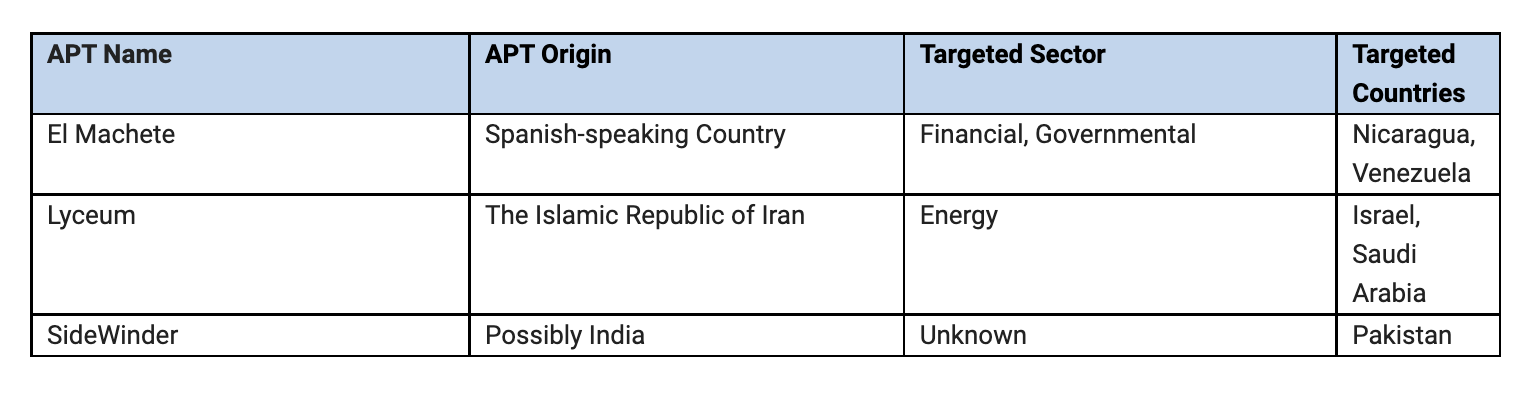
The threat intelligence arm of the organisation, Check Point Research (CPR), revealed three APT groups named El Machete, Lyceum and SideWinder were found to be running spear-phishing campaigns in five countries.
Key findings:
According to Sergey Shykevich, threat intelligence group manager at Check Point Software, the CPR team are seeing a variety of APT campaigns that utilises the current war for malware distribution right now.
“The campaigns are highly targeted and sophisticated, focusing on victims in the government, financial and energy sectors.
“In our newest report, we profile and bring examples from three different APT groups, who all originate in different parts of the world, that we caught orchestrating these spear-phishing campaigns.
“We studied the malware involved closely and found capabilities that span keylogging, screenshotting and more,” Shykevich said.
The attackers used decoys ranging from official-looking documents to news articles and job postings. After examining the lure documents, CPR found malware capable of keylogging, screenshotting and executing commands. CPR believes the motivation behind these recent cyber espionage campaigns is to steal sensitive information from governments, banks and energy companies.
The table below summarises each APT group’s origin, target sector and target countries.
Malware capabilities
CPR studied the malware laced by each of the three APT groups, specifically for these cyber espionage activities.
Capabilities include:
Attack Methodologies
El Machete
Lyceum
SideWinder
Russia-Ukraine-themed documents become lure of choice
El Machete was spotted sending spear-phishing emails to financial organisations in Nicaragua, with an attached Word document titled “Dark plans of the neo-Nazi regime in Ukraine”. The document contained an article written and published by Alexander Khokholikov, the Russian Ambassador to Nicaragua that discussed the Russo-Ukrainian conflict from the perspective of the Kremlin.

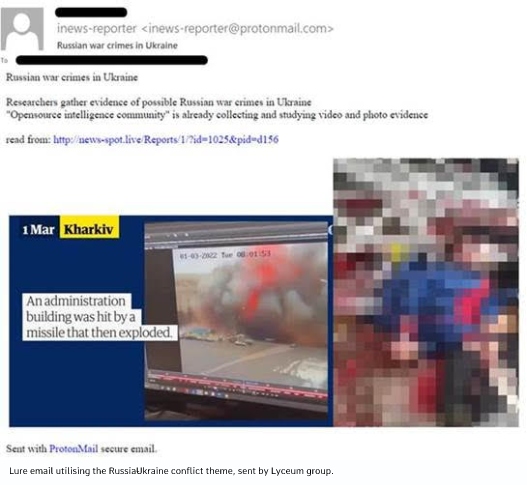
Lyceum
In mid-March, an Israeli energy company received an email from the address inews-reporter@protonmail[.]com with the subject “Russian war crimes in Ukraine”.
The email contained a few pictures taken from public media sources and contained a link to an article hosted on the news-spot[.]live domain. The link in the email leads to a document which contains the article “Researchers gather evidence of possible Russian war crimes in Ukraine” published by The Guardian. The same domain hosts a few more malicious documents related Russia as well as the Russia-Ukraine war, such as a copy of an article by The Atlantic Council from 2020 on Russian nuclear weapons, and a job posting for an “Extraction/Protective Agent” agent in Ukraine.

SideWinder
SideWinder’s malicious document, which also exploits the Russia-Ukraine war, was uploaded to VirusTotal (VT) in mid-March. Judging by its content, the intended targets are Pakistani entities; the bait document contains the document of the National Institute of Maritime Affairs of Bahria University in Islamabad and is titled “Focused talk on Russian Ukraine Conflict Impact on Pakistan”. This malicious document uses remote template injection. When it’s opened, the document retrieves a remote template from an actor-controlled server.

Latest overall cyber attack numbers on Ukraine, Russia and NATO countries
Recently, Check Point Research (CPR) released an update on cyber attack trends throughout the current Russia-Ukraine war. One month after the war started on 24 February 2022, both Russia and Ukraine saw increases in cyberattacks of 10 per cent and 17 per cent, respectively.
CPR has also observed a 16 per cent increase in cyber attacks globally throughout the current conflict. CPR shared cyber attack data for NATO countries, regions.
Shykevich added that CPR’s findings reveal a clear trend, that collateral around the war between Russia and Ukraine has become a lure of choice for threat groups worldwide.
“It is my strong belief that these campaigns are designed with the core motivation of cyber espionage.
“I strongly recommend governments, banks and energy companies to reiterate cyber awareness and education to employees, and to implement cyber security solutions that protect the network on all levels,” Shykevich said.
[Related: Vulnerability intelligence report reveals 136% increase in widely exploited security flaws]