Share this article on:
Group-IB's second annual Ransomware Uncovered 2021/2022 report has found that the average ransom demand grew by 45 per cent to approximately $247,000 in 2021.
A record-breaking ransom of $240 million ($30 million in 2020) was demanded by Hive from MediaMarkt.
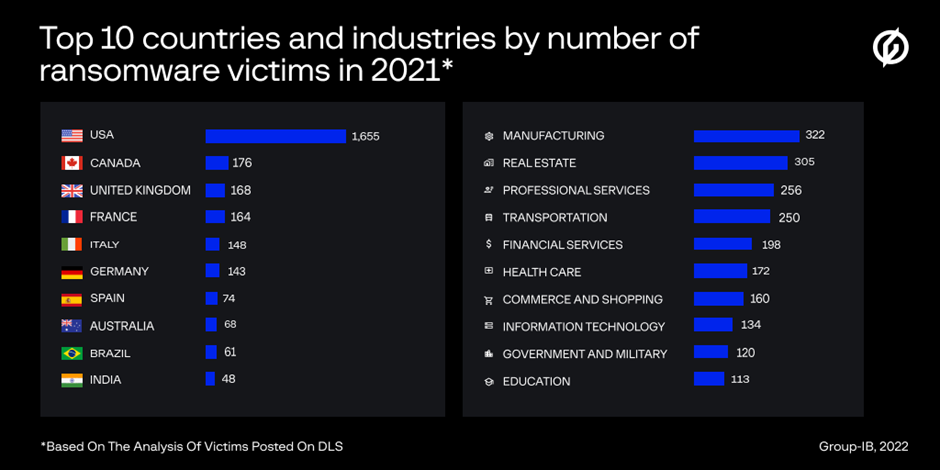
Between Q1 2021 and Q1 2022, APAC became the third most targeted region after North America and Europe based on the analysis of victim data posted on ransomware DLS, belonging to 335 companies from the Asia-Pacific region.
The “Top 10 Countries” in the Asia-Pacific by the number of victim-companies posted on DLS were Australia (68), India (48), Japan (32), China (30), Taiwan (22), Hong Kong (20), Thailand (19), Indonesia (17), Singapore (17), and Malaysia (14).
According to Oleg Skulkin, head of Group-IB DFIR team, rebrands from malicious actors and the merging of TTPs made it challenging for security professionals to keep track of the ever-evolving tactics and tools employed by ransomware threat actor.
“To help corporate cyber security navigate through and prepare for ransomware incidents we outlined the main trends and TTPs changes and turned them into actionable insights mapped to and organised according to the MITRE ATT&CK matrix,” Skulkin said.

Lockbit, Conti, and LV v.1 were the most aggressive ransomware gangs in Australia with 15, 12 and 8 victims from Australia posted on DLS, respectively.
The most frequently targeted industry verticals were professional services (11 companies posted on DLS), real estate (eight victim-companies), and commerce and shopping (six).
Human-operated ransomware attacks remained the most prominent cyber threat over the past three years, driven by the rise of initial access brokers and the expansion of RaaS programs.
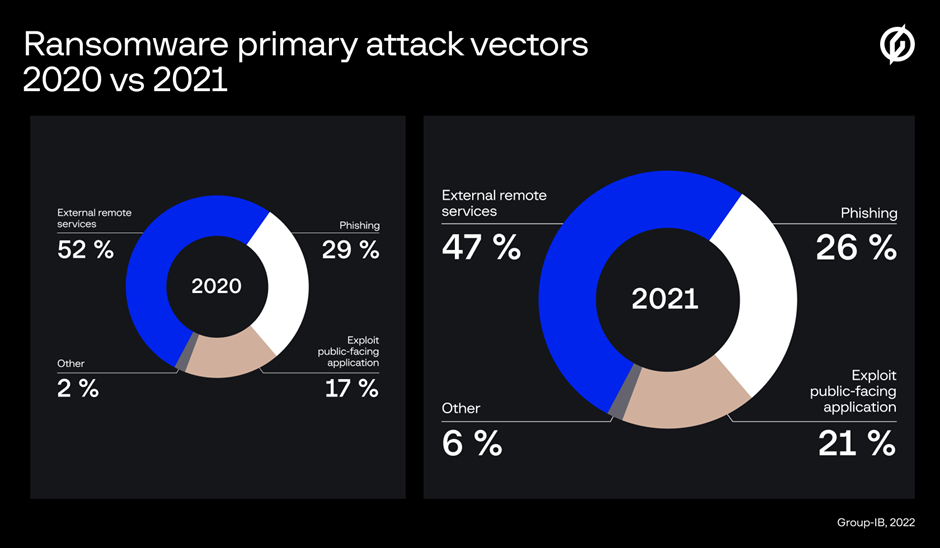
Exploiting public-facing RDP servers continued to be the most common method used to access the target network in 2021, with 47 per cent of all the attacks investigated by Group-IB DFIR launched by compromising an external remote service.
Spear phishing emails were the second most common form of attack (26 per cent), with the deployment of commodity malware becoming increasingly popular among ransomware actors.
Further, many ransomware affiliates leveraged 'living-off-the-land techniques' and legitimate tools during the attack life cycle, with commodity malware often used to start post-exploitation activities via loading frameworks such as Cobalt Strike (observed in 57 per cent of the attacks).
Other ransomware gangs were found to have deployed unconventional approaches, with REvil affiliates, for example, leveraging zero-day vulnerabilities to attack Kaseya’s clients.
[Related: Global IT leaders grapple with cloud transformation talent shortages]