Share this article on:
North Korean state-sponsored hacking group “Andariel” has been linked to the Maui ransomware operation that has been causing dissonance in South Korea.
Kaspersky researchers have linked state-sponsored North Korean hackers "Andariel" with the Maui ransomware operation with medium confidence.
The hacking collective is notorious for orchestrating campaigns with financial motives and according to Kaspersky, the group's overall strategic goals match with running their own ransomware operation.
In the past, Andariel has been tied to ransomware attacks targeting South Korean companies in media, construction, manufacturing, and network services.
Otherwise known as Stonefly, the Andariel group has also been observed to enact cyber attacks in order to perform espionage, data theft, data wiping, and operations to raise revenue for the North Korean government.
The groups targets include state, government and army organisations, and financial service providers, since it reportedly began operation 2015.
The US State Department announced rewards of up to $10 million for information about cyber actors, and Andariel was among the DPRK-backed hacking groups on the wanted list.
Based on build timestamps, Maui ransomware started attacks in April 2021 and has been observed to maintain a focus on healthcare organisations in the US.
The FBI and Cybersecurity and Infrastructure Security Agency (CISA) have previously shared warnings and indicators of compromise that pointed to North Korean threat actors, including the Maui ransomware.
US law enforcement agencies have been tracking Maui, and recently recovered approximately $500,000 of ransoms paid by hospitals to the ransomware gang.
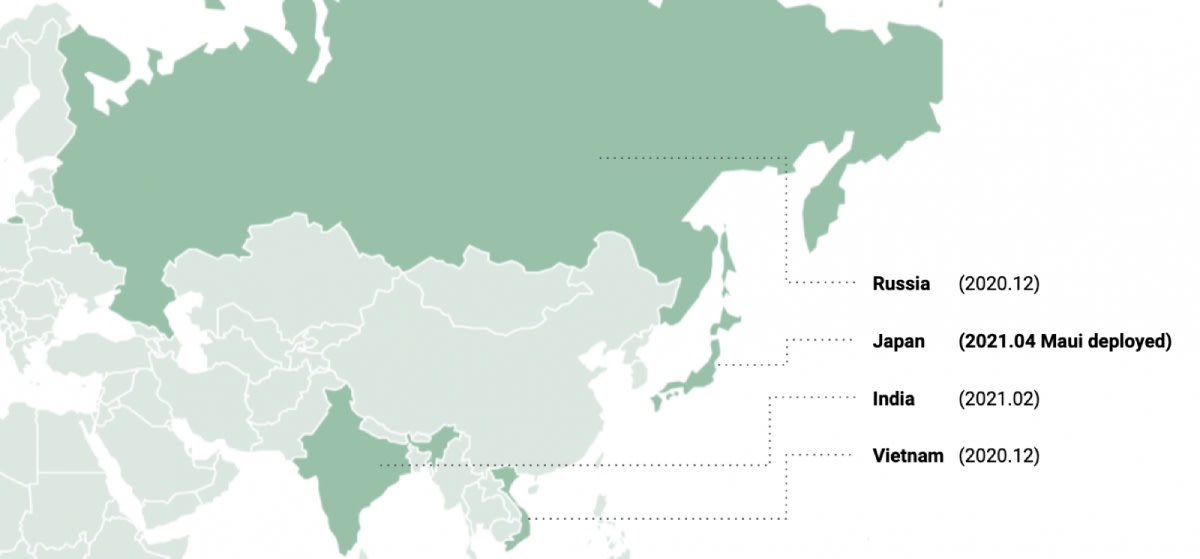
Outlining an earlier Maui attack against a Japanese housing company, Kaspersky researchers have found that the Japanese victim was hit by the DTrack malware mere hours before encryption, while subsequent log analysis revealed the presence of the "3Proxy" tool in the firm's network months earlier.
DTrack (also known as Preft) is a modular malware specialising in data theft and HTTP exfiltration via Windows commands. 3Proxy is a free open-source proxy server utility observed in various Andariel past campaigns.
Kaspersky researchers have linked previously unattributed attacks in India, Russia, and Vietnam to Andariel operations, as the DTrack variant used in all attacks feature a code similarity of 84 per cent to samples directly linked to previous Andariel operations.
The malware used against the Japanese firm employed the same shellcode reported in a 2021 Symantec write-up that analysed an Andariel campaign.
Additionally, the initial network compromise methods noticed in these attacks also feature typical Andariel characteristics, like exploiting vulnerable Weblogic servers (CVE-2017-10271). Kaspersky researchers also noted that its analysts have seen identical exploits and methods of compromise used by Andariel in mid-2019.
While the APT and the ransomware operation appear to have a connection, the above isn't enough for concrete attribution, however, building upon previous revelations presents evidence that could help with early detection and prevention according to Kaspersky.
[Related: Federal Court orders Google LLC to pay $60m for misleading data collection]